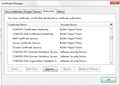
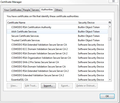
Insecure Connection because Certicicate Authorities is not up to date
We have multiple computers that some website work on some computers and don't work on others. They can be on the same exact version of Mozilla, but certain sites get the Insecure connection. But you go to the computer next to it the site works just fine. I noticed the Certificate Authorities list are not the same. How does this get updated? How do I update the computers that don't have full list?
Attached are a comparison of two computers in our network.
I have tried uninstalling and reinstalling, but still has same list. example would be datalocker.com
I am not looking to only add the certificate for this site. I know how to add one exception if I trust the site. The problem is multiple sites do it and I shouldn't have to add one for every single site. If other computers can access just fine, then there should be a way to update the list without individually adding each site.
Modified
All Replies (12)
hi, on the datalocker.com example, that's a failure on the part of the website in question. they use an intermediate certificate (not one that is trusted by the browser by default) but fail to provide a certification path to a known trusted authority - see https://www.ssllabs.com/ssltest/analyze.html?d=datalocker.com&hideResults=on ("Chain issues: Incomplete")
firefox caches intermediate certificates that are properly implemented, as you surf along - so in this case it will depend on chance if datalocker.com works or not (or actually if firefox on a particular device has come across any other site that has properly implemented the "COMODO RSA Extended Validation Secure Server CA" intermediate certificate). please contact the webmaster of that website, as it would be up to them to fix this issue...
Did you verify that the server sends all intermediate certificates needed to build a complete certificate chain?
- Server test: https://www.ssllabs.com/ssltest/
Firefox automatically stores intermediate certificates that servers send in the Certificate Manager for future use. Stored intermediate certificates show as "Software Security Device" in the "Security Device" column in the Certificate Manager. A server needs to send the full certificate chain that includes all required intermediate certificates. If a server doesn't send a full certificate chain then you wouldn't get an untrusted error if Firefox has stored missing intermediate certificates by visiting a server in the past that has send this certificate, but you do get an untrusted error if this intermediate certificate isn't stored yet.
So my list certificates is longer because I have come across a site with certificate correctly before and it saved it?
My computer doesn't have safe browsing on, but we turned on for majority of our users. They seem to be the ones that keep having issues.
Does firefox cache intermediate certificates if safe browsing has been turned on?
Just hard to troubleshoot with users when they get that message and my computer don't. Only main difference is the Safe-Browsing is enabled on there machines and not on mine. Other than that we have same settings and same version.
This has started happening a lot lately so trying to figure out why there list isn't updating. It is not just there site I have issue with, I am looking through old help desk tickets to find the other sites to see if it is same issue.
All the sites I was previously having issues with seem to be working now, so I can't give a second example, maybe it was on there end before, recent site issues were: https://laors2.laworks.net/lawats/ https://commerce.unisourcelink.com/ec/Home.do?ts=0 https://securemail.johndeere.com/formpostdir/safeformpost.aspx
John Deere one is still not working
Modified
Quick solution for the fix was to use IE, but we prefer for our users to use Mozilla if possible, so I am just trying to get ahead of the issue.
Modified
Joshua_Calais said
My computer doesn't have safe browsing on, but we turned on for majority of our users. They seem to be the ones that keep having issues.
Sorry, what is safe browsing? The check against a list of known phishing/malware sites? I can't think of any way that should be related to validating SSL certificates.
Sorry Private Browsing, it is the Tools->Options->Privacy->History
You have the average user defaulted to automatic private browsing? I wonder if that has any effect on whether intermediate certificates are saved to cert8.db. (I wonder, but can't test at the moment...)
You can't create a permanent exception if the page is opened in Private Browsing mode (automatic and via New Private Window) and send intermediate certificates aren't stored in the Certificate Manager as well.
Want to make sure I am fully understanding, we have a few things going on.
My computer is not in Private Browsing Mode, so my computer stores intermediate Certificates and that is way my l list is longer than my users list of certificates, correct? Next the website we were accessing had a incomplete certificate so my computer saw it already had the certificate once before and allowed me to access the site even though the sites certificate was incomplete, correct?
Then my users since they have private browsing on, when they reach the site with the incomplete certificate it just fails because they don't have a previous instant of a valid certificate to reference, correct?
This means my users can only access sites that have valid certificates, if not they are going to get the unsecure message?
Also, when the users had issues I tried unchecking the private browsing to see if they could access site and still failed. But I guess this makes more sense now. Even though I unchecked private browsing, they still would not have valid certificate in there history and the sites current website had an incomplete certificate, so accessing would still fail, correct?
Modified
Hi Joshua_Calais, Firefox is looking for an unbroken chain of trust from the site's certificate -- which itself is fine -- to a trusted root. When a site does not sending the intermediate signing certificate(s) to complete the chain of trust, Firefox checks its own certificate store to see whether it already has validated the missing certificate(s). Unlike some other browsers, Firefox does not search out a missing certificate from other sources.
Based on what I've read in this thread, In PB mode, Firefox does not accumulate valid intermediate certificates as it validates them, presumably because such certificates sometimes have a site-specific issuer (like Amazon, AOL, Google, etc.).
The Apache version can make a difference.
I have an owncloud setup on 2.4 and it didn't need a separate SSLCertificateChainFile entry, but an almost identical setup on 2.2 did.
The 2.2 setup has two entries to the same file: SSLCertificateFile (exact_amefile) SSLCertificateChainFile (exact_samefile)